Ultimate Guide to Preventing SYN Flood Attacks
In the ever-evolving world of cybersecurity, businesses and individuals must remain vigilant against a range of potential threats that can disrupt operations, damage reputations, and lead to significant financial loss. Among these threats, SYN Flood attacks stand out as one of the most prevalent and damaging forms of Denial of Service (DoS) attacks. Understanding what SYN Flooding is, how it works, and most importantly, how to prevent it, is essential to securing your network.
In this comprehensive guide, we will cover everything you need to know about SYN Flooding, its mechanisms, the potential risks it poses.
What is a SYN Flood Attack?
A SYN Flood is a type of Denial of Service (DoS) attack that targets the TCP handshake process. To understand how SYN Flooding works, it’s important to know how the standard TCP three-way handshake functions.
When two computers (like a client and a server) communicate over the internet, they establish a connection using a handshake process:
- SYN – The client sends a synchronization request to the server.
- SYN-ACK – The server responds with a synchronization acknowledgment.
- ACK – The client responds back, completing the handshake and establishing the connection.
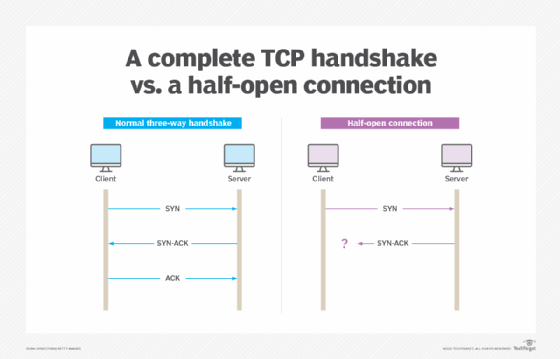
In a SYN Flood attack, the attacker sends a large volume of SYN requests to a server but does not respond to the SYN-ACK responses. As a result, the server’s resources are exhausted, and it is unable to complete the handshake process with legitimate users. This leads to a denial of service, rendering the server inaccessible to genuine requests.
The Consequences of SYN Flood Attacks
SYN Flooding can have severe repercussions for businesses and organizations that rely on their web presence for daily operations. The consequences may include:
- Website Downtime: A server overwhelmed by a SYN Flood attack will be unable to serve legitimate requests, causing your website or service to go offline.
- Loss of Revenue: If your business operates online, downtime can result in lost sales, customers, and revenue.
- Damage to Reputation: Prolonged or repeated outages due to SYN Flooding can erode customer trust and damage your brand’s reputation.
How to Prevent SYN Flood Attacks: Essential Protection Strategies
Preventing SYN Flood attacks requires a multi-layered approach. Whether you are hosting your site with a provider or managing your own infrastructure, there are crucial steps you can take to secure your system and minimize the risk of such attacks.
1. Select a Reliable Hosting Provider with DDoS Protection
Choosing the right hosting provider can make a world of difference in your ability to defend against SYN Flood attacks. When evaluating hosting options, consider the following:
- DDoS Protection: Look for providers that offer DDoS protection as a standard feature. These services help mitigate the impact of SYN Floods and other types of denial-of-service attacks.
- High Availability Infrastructure: Choose providers with robust infrastructure, including load balancers, redundant servers, and geographically distributed data centers. This setup can help handle traffic spikes and ensure service continuity.
- Traffic Filtering and Rate Limiting: A good hosting provider will implement rate-limiting and traffic filtering to screen out malicious traffic before it reaches your server.
By partnering with the best hosting providers that include these features, you can ensure that your infrastructure remains resilient even when under attack.
2. Self-Hosting: Configuring Your Server for SYN Flood Mitigation
If you are hosting your server on-premises or in a private data center, implementing SYN Flood protection becomes your responsibility. Fortunately, there are several techniques you can use to secure your infrastructure:
a) Configure SYN Cookies
SYN Cookies are a technique used to defend against SYN Flood attacks by encoding the sequence number in the initial SYN response. This allows the server to handle a large volume of requests without allocating system resources until the handshake is completed. It ensures that the server does not reserve memory or connections for incomplete requests.
b) Increase Backlog Queue Size
The backlog queue is the list of half-open connections waiting to be processed. During a SYN Flood attack, the queue gets overwhelmed with incomplete requests. By increasing the size of the backlog queue, you can ensure that more requests are handled without dropping legitimate connections.
c) Implement Connection Limiting
Another effective defense is to limit the number of connections allowed from a single IP address in a short period. By doing so, you reduce the ability of attackers to flood your server with an overwhelming number of SYN requests.
3. Leverage Advanced Security Tools
In addition to basic server configurations, you can implement specialized security tools designed to mitigate SYN Flood attacks:
- Traffic Anomaly Detection: Deploy intrusion detection systems (IDS) and intrusion prevention systems (IPS) to identify and block abnormal traffic associated with SYN Floods.
- Rate Limiting and Load Balancing: Use load balancers to distribute incoming traffic across multiple servers, preventing any single server from becoming overloaded during a SYN Flood.
Final Thoughts: SYN Flooding Doesn’t Have to Be a Threat
The risk of SYN Flooding is real, but with the right strategies in place, you can significantly reduce your exposure. Whether you’re hosting with a provider or managing your own infrastructure, staying proactive in securing your network will help protect your website, reputation, and bottom line.
By selecting the right provider or configuring your own system with effective protections, you can maintain optimal performance and resilience. Be vigilant, be prepared, and you’ll ensure that your network is always secure, no matter the attack vector.