What is Cross-site Scripting?
What is Cross-site Scripting(XSS)?
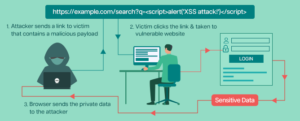
Cross-site Scripting (XSS) is a type of security vulnerability commonly found in web applications in which an attacker injects malicious scripts into a trusted website. The attacker sends malicious links into user-provided input. These malicious scripts are then executed in the context of the victim’s browser, allowing the attacker to steal information, redirect a user to a malicious website, hijack user sessions, or perform other malicious actions.
Reflected XSS: This kind of attack involves injecting malicious code into the online application, which the server then reflects back to the user. This frequently occurs via a form entry or URL parameter.
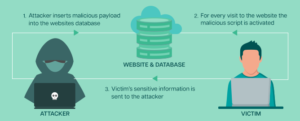
Stored XSS: This happens when a malicious script is kept on the server (in a database) and is subsequently served to several users each time they visit the resource or page that is affected.
DOM-based XSS: Rather than on the server, the vulnerability appears in the client-side code, which is usually JavaScript. Because the malicious script modifies the Document Object Model (DOM) in an insecure way, it gets executed in the victim’s browser.
How can we avoid XSS Vulnerability?
Use input validation.
One of the best defenses against XSS attacks is to implement input validation. This entails verifying that user input is in the correct format and is free of any questionable characters or script code.
Put output encoding in place
Implementing output encoding, which entails encoding user input so that the browser does not read it as script code, is another technique to stop cross-site scripting assaults.
Use a CSP, or content security policy.
One security feature that lets you limit the kinds of content your web application can load is called a Content Security Policy (CSP). By putting in place a CSP, you can stop dangerous scripts from running on your website.
Update the software used in web applications.
The program has to be updated to the newest version or patched with the most recent security patches if the vulnerability stems from an outdated or weak web application.
Use a firewall for web applications (WAF)
XSS attacks can also be avoided with the aid of a web application firewall (WAF), such as AppTrana, which filters out malicious payloads prior to them entering the online application.
XSS attacks can have detrimental effects, such as the dissemination of malware, the defacement of websites, and the theft of private data like cookies or session tokens. Implementing security measures like Content Security Policy (CSP) and performing appropriate input validation and output encoding are necessary to prevent XSS vulnerabilities.